Salesforce Security is both powerful and flexible. To be both makes the security configuration somewhat complex. I thought it best to talk about, at a high-level, the different security elements in the Salesforce Security Model. And since we recently talked about security of your data in the cloud, I figured this topic was completely appropriate.
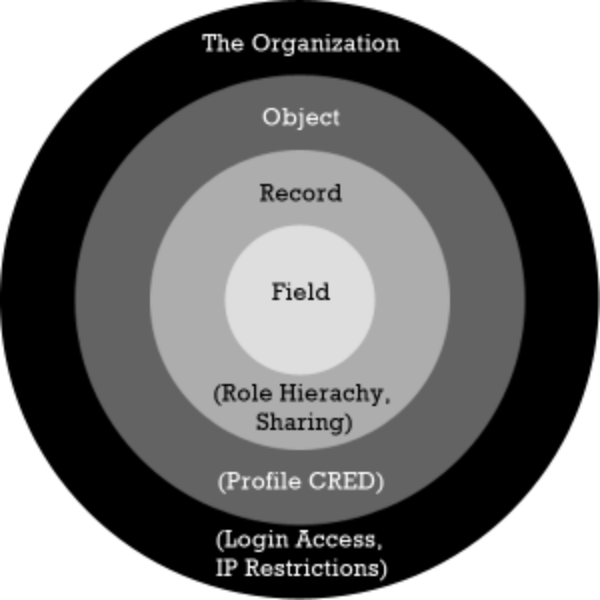
Security can be grouped into four logical tiers, The Organization, Objects, Records, and Fields. Each Tier is a different degree of specificity, like a broad to narrow brush stroke. As you move inward in the circle the security settings become more precise.
Organization-level Security:
This is the broadest brush stroke of all security settings. At the organizational level you can can establish when and from where your users can access the system.
Using Trusted IP Ranges, you can limit your users ability to login only when they are in the office. When your users login from an IP address within the specified range, they gain access to your org without requiring activation. If they attempt to login from outside the trusted range, they will be challenged in the form of two-factor authentication. Typically they will be asked to enter in a code sent to their mobile device. This prevents unwanted access but still provides your sales reps access when they are working from the road. To configure this, simply go to Setup > Security Controls > Network Access, and enter the necessary IP Ranges.
If you have Enterprise edition or higher you can also set IP Restrictions on individual User Profiles, enabling flexible access for different users. However, when IP Ranges are specified on the Profile, if a user assigned to that Profile attempts to login outside the trusted range, they will not be challenged, they will simply be denied access. This might be a useful feature to limit either your inside sales reps or support group to access only when they are in the office, but not for your outside reps that need access all the time. To Configure go to Setup > Profiles > [Profile Name] > Login IP Ranges.
Also available with Enterprise edition is the ability to limit profile access to specific times of the day. So you may want to limit support user access to 8am - 6pm Monday through Friday, but not weekends. You may want to give your sales reps unfettered access during the week but still restrict access on weekends. This is all doable by setting login hours for Profiles. To Configure go to Setup > Profiles > [Profile Name] > Login Hours
Object-level Security:
Object-level security is controlled by the Profile assigned to the user. The Profile is the crux of the security model. It controls what types of data a user can see i.e. Objects, and what they can do in those Objects. These settings are known as CRED (Create, Read, Edit, Delete). Every user is associated to a profile. In Professional edition you will only have access to the standard profiles and they cannot be modified. In Enterprise and higher you have full reign to modify or create whole new profiles for specific purposes.
If you have Enterprise or higher you also have access to something called Permission Sets. This is a very powerful piece of functionality to give you an even finer adjustment of security. If most users require the same base level access but there are occasional groups of users that require one-off functionality and/or access, you can grant them those permissions with Permission Sets. This avoids the need to create dozens of different profiles for each exception. With Permission Sets you can temporarily grant access for specific tasks then remove them just as easily without having to change a user's Profile.
Additional things you can control through Profiles are what apps a user has access to, which tabs they will see by default and which ones are hidden, numerous system permissions such as API access, Mass Email, Modify All Data, etc, and their login hours and IP ranges as mentioned above.
Record-level Security:
Profiles control your overall access to the data i.e. can you see it or not, and what can you do to it. Record level-security controls which records in the data you have access to. If your Profile doesn't give you access to an Object it doesn't matter if you have access to the records, you still can't see them because of the limits in your Profile. Access to records comes in flavors:
- Public Read/Write/Transfer
- Public Read/Write
- Public Read Only
- Private
Record-level access can be granted by establishing various sharing rules. Sharing is caring!
The creator/owner of a record will have full access to a record. Beyond that, access to records is controlled by Sharing settings (Setup > Security Controls > Sharing Settings). This is configured in one of two ways, with Roles, in the Role Hierarchy or by Sharing Rules.
By establishing a Role Hierarchy (Setup > Manage Users > Roles), full access to a user's records is afforded to users who are above that user in the hierarchy.
You can alter the default sharing settings to open up or restrict the access as much as you want. You can also create specific sharing occasions. If you have two parallel roles in the role hierarchy, East Coast Sales, and West Coast Sales, you can establish a sharing rule to give visibility to each other's leads.
So the Role Hierarchy gives vertical access to records to users above you in your org and sharing rules give horizontal access to records across your organization.
Field-level Security:
The final and most detailed level of security is access to individual fields. Field-level security is only configurable on a given profile. As such, this ability is limited to Enterprise Edition and higher.
Field-level security can only restrict access, it cannot grant it. For example, if you only have Read Access on the Leads Object, but grant a Profile Read and Edit access on a Field in the Leads Object, the users assigned to that Profile will still only have Read access. However, if a Profile has Read and Edit permissions on the Leads Object and, Read only field-level permissions on a field in the Leads Object, then users assigned to that profile will only have Read access.
So that's it. Salesforce.com security in a nutshell. Obviously it is much more detailed and nuanced but this should provide you a 30,000 foot view and provide some context. If you're not still scratching your head, and actually thirsty for more, Salesforce has a great new 9-part Youtube Series on Security called "Who Sees What" that I think does a great job of explaining their complex security model.
Have Questions? Leave a comment below. We will get back to you with an answer.
Know someone else who might benefit from knowing what we know? Please share us with your friends.
We've got the know-how
And we want to share it with you. Join our mailing list and you'll get all sorts of good info delivered conveniently to your inbox. (Not to worry your email will remain securely with us).